Figure one: Which domains ought to be managed by you and which may be opportunity phishing or area-squatting attempts?
Insider threats are A different one of those human troubles. In lieu of a risk coming from beyond a company, it emanates from within just. Menace actors may be nefarious or just negligent persons, however the risk arises from somebody who now has use of your delicate info.
Threats are likely security dangers, even though attacks are exploitations of such threats; genuine makes an attempt to exploit vulnerabilities.
Given that We've got described An important things which make up a company’s (exterior) danger landscape, we could take a look at tips on how to identify your very own risk landscape and lessen it inside of a specific method.
Successful attack surface management needs an extensive knowledge of the surface's belongings, like community interfaces, application applications, as well as human components.
Lack of physical security. Certainly, whether or not your iPhone locks right after two minutes of idleness, that doesn’t mean it’s Protected from prying eyes when still left while in the airport lavatory.
Procedures are tied to rational segments, so any workload migration may even move the security procedures.
Distinguishing in between menace surface and attack surface, two normally interchanged terms is important in comprehension cybersecurity dynamics. The threat surface encompasses every one of the possible threats that will exploit vulnerabilities in the procedure, which includes malware, phishing, and insider threats.
It is just a stark reminder that strong cybersecurity actions ought to prolong outside of the digital frontier, encompassing thorough Bodily security protocols to guard versus all kinds of intrusion.
They then have to categorize every one of the possible storage locations in their company data and divide them into cloud, equipment, and on-premises methods. Businesses can then assess which consumers have use of info and resources and the level of accessibility they possess.
As the risk landscape continues to evolve, cybersecurity methods are evolving that can help corporations stay guarded. Using the most recent AI for cybersecurity, the AI-run unified SecOps platform from Microsoft offers an integrated approach to menace avoidance, detection, and response.
State-of-the-art persistent threats are Those people cyber incidents that make the notorious list. They're prolonged, refined attacks executed by threat actors having an abundance of means at their disposal.
Take into account a multinational Company with a fancy network of cloud companies, legacy techniques, Cyber Security and third-occasion integrations. Each of such factors signifies a possible entry level for attackers.
Proactively regulate the digital attack surface: Obtain full visibility into all externally dealing with assets and be certain that they are managed and protected.
 Anna Chlumsky Then & Now!
Anna Chlumsky Then & Now!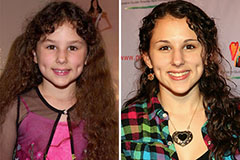 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now!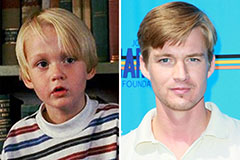 Mason Gamble Then & Now!
Mason Gamble Then & Now!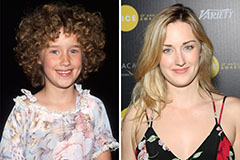 Ashley Johnson Then & Now!
Ashley Johnson Then & Now! McKayla Maroney Then & Now!
McKayla Maroney Then & Now!